One of the main advantages that ACI offers is the ability to simplify the configuration, and the ability to backup, your entire datacenter configuration.
In a traditional datacenter network, backups must occur on a box-by-box basis (leading to configuration sprawl), and the process to back them up is generally managed by a combination of network engineering and server admin resources.
With ACI, all components of the ACI Fabric are treated as one entity (Leafs, Spines, APIC controllers). The ACI Fabric configuration (while made up of different managed objects) is combined into one tar/gz zipfile, which greatly improves the configuration backup process, and the configuration restoration process. Finally, the backups we create can be configured as one time backup jobs, or we can schedule a daily or weekly scheduler to export our entire Fabric configuration to an remote location (i.e., external server) using SCP, FTP, or SFTP.
Configuration Steps for one-time backup
- Create a remote location – Where do you want the configuration to be stored
- Create a configuration export policy
- (optional) – Configuration Global AES Encryption
Creating a remote location
- Enter a name for your remote location
- Enter the hostname or IP address of your remote server
- Select your protocol (SCP/FTP/SFTP)
- Enter the remote path < Failure to enter this correctly will lead to an error (Upload failed, Error in the SSH layer)
- Verify the Remote Port is correct
- Enter Username
- Specify password / Public Key
- Enter Password
Admin > Import/Export > Remote Location

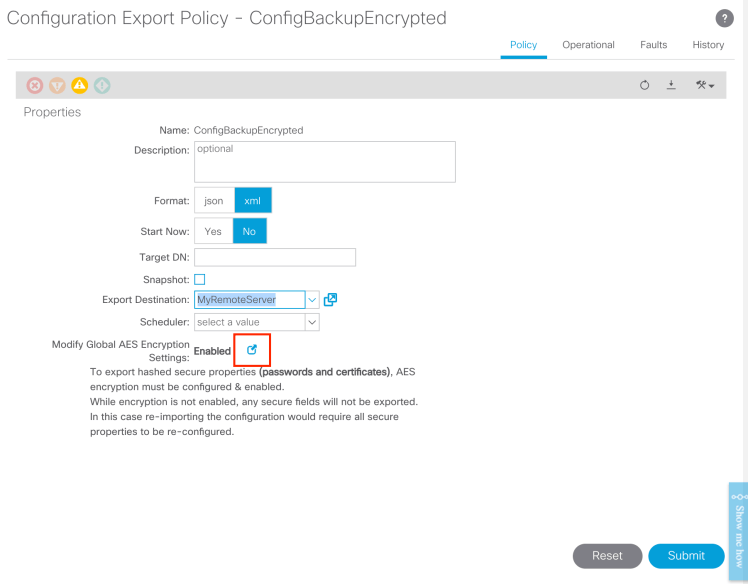
Creating a Configuration Export Policy
- Name your Export Policy
- Select your export format (XML/JSON)
- Start now (this will force an export immediately)
- Pick your Export Destination (this will be the remote location you defined earlier)
- (optional) Scheduler (this could be configured if you want recurring (daily) backups. This would NOT be enabled if you selected “start now” option
- (optional) Enable Global AES Encryption Settings
Admin > Import/Export > Export Policies > Configuration

(optional) Enable Global AES Encryption Setting
“To export hashed secure properties (passwords and certificates), AES encryption must be configured & enabled. While encryption is not enabled, any secure fields will not be exported. In this case re-importing the configuration would require all secure properties to be re-configured.”
If you do not enable the Global AES Encryption and export a configuration, when you try to re-import the configuration, passwords for things such as VMM Integration (i.e., your vcenter username/password) will not be re-imported, and would have to be re-entered before VMM Integration would be functional. I highly recommend that you enable the Global AES Encryption.
- Enable the encryption
- Configure a passphrase – THIS HAS TO BE A 16-digit (or longer) passphrase.
- REMEMBER THE PASSPHRASE – If you forget this, and need to re-import, you will be out of luck. One trick I use is using the local admin password, and copying it into the passphrase twice. (i.e., Cisco123Cisco123)

Verification
In order to check on the status of your back, from your Export Configuration, select the Operational tab.
Admin > Import/Export > Export Policies > Configuration > YourConfigExport

2 thoughts on “Creating a backup for your APIC Cluster”